Cybersecurity is often not top of mind for small business owners. However, it should be. 43% of cyber-attacks target small businesses—since COVID-19, cyber-attacks are up 300%. For very small businesses, protecting your business is often straightforward—avoid phishing scams and change passwords frequently. However, as your business grows, so does the complexity and need for quality cybersecurity.
If you’re new to cybersecurity and need to familiarize yourself with industry terms, review our glossary in this article.
1. Train Your Employees
One of the most-important takeaways from this list is that human error accounts for 95% of successful cyber-attacks—an employee clicks a link in a suspicious email, or a disgruntled employee causes damage to data.
You need to ensure you and your employees are aware of potential threats, then, what to do during a computer breach or infection.
If you’re creating a training program, consider the following key points:
Key Points:
- What makes a secure password?
- What are phishing and social engineering attacks and how to avoid them?
- How to browse online securely?
- How to identify a suspicious link?
- Who to contact if you suspect or experience a cyberattack, including potential phishing schemes?
- How to secure a home network—especially for remote workers?
- How and when to use any company supplied or approved cybersecurity programs, such as antivirus and password managers?
The training should be ongoing: New threats and schemes pop up all the time. Consider having a regular monthly bulletin about the latest threats. Some businesses even send out fake attacks, such as a fraudulent email phishing scheme, to check how well prepared they are.
Train Employees About Email Phishing Scams
The most common small business cybersecurity threat is phishing scams, which are emails intended to steal usernames, passwords, and sensitive information such as a credit card.
The majority of small business cybersecurity challenges come from this issue—employees responding to a scam and giving away private information via email. Unfortunately, due to the increase in remote work, these scams are on the rise.
Currently, one of the most frequent threats is for a hacker to imitate a boss’s email and ask an employee to purchase gift cards or transfer funds for an event or function.
Train your employees to be suspicious of these emails—anything that asks them to do something outside their usual duties or that involves sending money or confidential information.
Common ways to spot phishing scams include:
- Unfamiliar or wrong domain names in the email address
- Links in the email that are odd, overlong, or bizarre. For example, if you are given a link to Amazon, when you hover over the text, it should start with “Amazon.com,” not a variation.
2. Protect Your Passwords
Passwords are like keys—you have to protect them. However, unlike keys, it’s easier to get a copy. You and your employees must practice adequate password security so that if someone does get your password, it’s unlikely to affect your business drastically.
The first password tip is not using the same one repeatedly—have a unique password that’s different for every account.
A secure password should:
- Contain at least 10 characters
- Include a number
- Have both capital and lowercase letters
- A special symbol (!@#$%)
- Not include personal information—think birthday or dog’s name
Make sure your employees follow these recommendations as well. Everyone should change all their passwords (or at least the most vital ones) regularly—once every three months. We’ve all done this, but make sure it’s not the same password with a different number at the end.
This password management process can get time-consuming. There are trusted programs, called password managers. For example, RoboForm for Business, can even remind your employees to change their passwords according to a schedule you set.
As an alternative, have your IT or admin manager send out regular reminders. If you have a project management software, consider making password resets a recurring task.
3. Purchase Antivirus Software
Antivirus software protects your computer against malware (any software with an intent to harm) by scanning the data traveling over the network or internet to your device. It is programmed with known threats and monitors all programs’ behaviors to flag suspicious behavior, block malware, and remove it if possible. It may also alert you to other, lower-priority threats.
The key to remember here is known malware and threats. Antivirus software gets continuously updated with the latest information, so you have to keep it up-to-date.
Most operating systems include reasonably good antivirus software, but businesses should get an additional antivirus program—even if you use Mac. You should also purchase it rather than depend on freeware (a free version).
Purchased programs include additional features like firewalls, web protection, password managers, and VPNs to keep your data secure. Antivirus software can cost anywhere from $10 to $100 per license, per year.
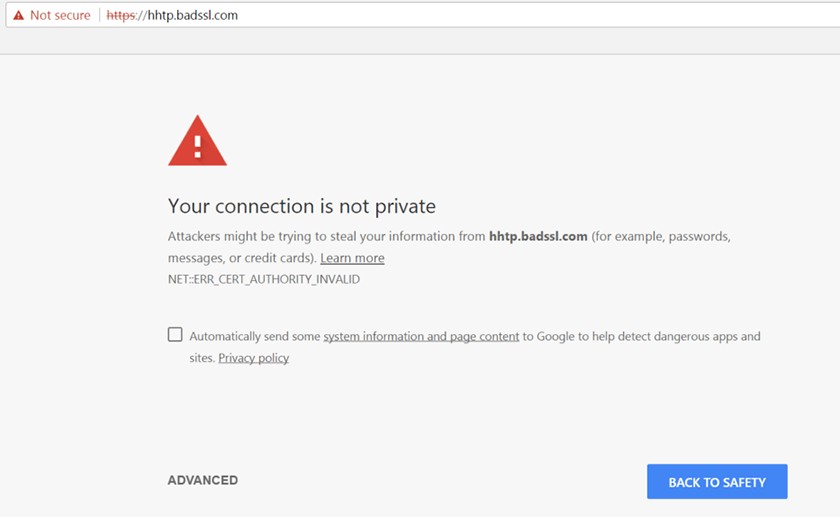
4. Make Sure Your Website Is HTTPS
HTTPS websites have an additional layer of encryption for security. Not only is this important for fending off cyberattacks through your website, Google is now penalizing websites that lack this extra security, which could affect your site’s ranking in search results.
If you already have your SSL certificate, you need to install it on your web hosting account and link it to your website. Many web hosts will do this free or for a small fee.
If you’re starting a new business
and are creating your first website, it’s likely the SSL cert is already added. Older websites need to make this update to their website.
5. Backup All Data
Backing up data won’t prevent a cybersecurity breach, but it will make recovery easier. You should create a system in your business to back up all business data regularly. Fortunately, many programs let you do this automatically, so the responsibility doesn’t fall on you or employees to make copies.
If you prefer to keep information on-site (not in the cloud), an external hard drive or server can regularly backup and hold copies of data. Some security programs like Norton allow you to schedule regular backups of a computer to an external location.
You can also elect to back up to the cloud. This more robust cloud-backup is different from “cloud-based solutions” like Office 365, storing files in the cloud. Cloud-backups regularly copy all the data on a computer unless specifically told what types of files to save.
Cloud-based backup solutions like Carbonite operate in the background and are transparent to employees. It protects not only against attacks that might corrupt your server but also physical damage since most cloud-servers save in alternate locations. Look for cloud-based solutions with both physical and cybersecurity and licensing, including encryption and TLS protocols.
6. Keep Software and Website Updated
Sometimes, people resist updating software because they are comfortable with the interface of the older version. However, software companies (not just those for antivirus programs) update their software to close security gaps they’ve discovered in their programs.
Keeping your technology up to date applies particularly if you have a WordPress website. Hackers often infiltrate a site through outdated WordPress themes and plugins. If you manage your website, make sure you log in every three months and check if there are any updates.
7. Create a Small Business Cybersecurity Plan
Cybersecurity plans should give your business direction for routine maintenance. It should also outline what to do if a threat or hack occurs against the business. The plan needs to address not only how to protect your computers and servers, but how to address stolen employee, customer, and vendor sensitive information.
You should have a plan in place, a team to enact it, and a regular review to make sure that if something happens, no one is scrambling to figure out what to do.
Since attacks are computer-based, it’s a good idea to have the plan and checklists printed and kept up-to-date.
Include the following in your cybersecurity plan:
- Team: You should, at the very least, have a team leader, legal counsel, someone in IT, and a point of contact to reach out to any involved parties. One person may have multiple roles.
- External sources: These are people you contact for outside assistance like computer forensics experts to repair the damage, marketing professionals to issue statements, and your cyber-insurance broker for loss claims.
- List of potentially affected parties: If your data is compromised, who is affected? Consider employees, customers, vendors, and what privacy information you hold for each.
- List of other sensitive information: Do you have confidential documents that could be compromised?
- List of legal obligations and deadlines: By law, who must you contact and how soon?
- Create checklists for specific breach scenarios:
- Time and date of the breach
- Who to be contacted
- Establishing a virtual or physical perimeter around affected systems
- Taking the affected system offline if needed
- Interviewing those with critical knowledge of the breach
- Making a secure copy of the affected system so it can be fixed without tainting the assessment
- Action items to minimize damage and set up future safeguards
- Reporting the breach to state, local, and federal government agencies
- Recovery metrics: These are your goals and milestones, to track progress for reporting to customers, your board of directors, or the public as needed.
8. Secure Wi-Fi
Securing Wi-Fi protects against online threats by encrypting and password-protecting your internet connection. If you have a public Wi-Fi, you must make sure it’s challenging to hack. To get this security, you typically will purchase a modem with additional Wi-Fi features from your internet provider.
A secure Wi-Fi will also detect and alert you if you try to navigate to risky websites. It blocks malicious traffic or unwanted remote access from devices, including smartphones. It is not a replacement for antivirus software, but an additional layer of security.
Public Wi-Fi
With the use of smartphones and tablets for business, it’s tempting to log in to a public Wi-Fi to get work done when out of the office, but you should discourage employees from doing this—the connections may not be secure.
A hacker can infiltrate a computer through the unprotected, public Wi-Fi. Even secure public Wi-Fi should be suspect. You do not know the level of security or what the securing business is monitoring or recording.
9. Get a VPN Service
A VPN (virtual private network) is a way to secure an internet connection from a public internet connection.
If you have employees working remotely with sensitive data, you should consider getting a VPN to provide a secure, encrypted tunnel between the home user and the remote server. The VPN masks your employee’s IP address—this makes it harder for hackers to gain private information.
Avoid free VPN services, which often make their money by selling your data to third parties.
10. Protect All Devices
All company smartphones and tablets should be secured. When possible, supply employees with business devices. This business vs personal separation keeps sensitive business data off an employee’s personal device.
If this is not possible, employees should avoid storing business information on any device they share with family, friends, or housemates. Also, they should always lock devices with a PIN or password. Try to get employees to practice the same level of cybersecurity on personal devices as they do in the office:
- Keep programs updated
- Use encryption when possible
- Back up data
- Use an antivirus program
11. Get Cyber Liability Insurance
Cyber liability insurance protects businesses from losses or damage caused by cyberattacks and data breaches.
Consider cyber insurance if you:
- Deal with credit card payments
- Store confidential information vital to your company
- Are at a higher risk because of at-home employees
Costs vary depending on your risk factors and the coverage you choose. Small businesses with moderate risk usually pay from $1,000 to $2,500 per year.
There are two kinds of cyber liability insurance coverage:
- First-party coverage pays for costs incurred by your business such as customer notification, forensic services to repair the damage, or lost income from halting operations while you fix the problem. You may have some of this covered in your regular business insurance.
- Third-party (liability) covers losses incurred by your customers. These expenses include attorney fees, settlements against your company, government fines, and defense before regulatory boards.
12. Outsource Cybersecurity To a Managed Security Provider
Cybersecurity can be a complex undertaking. If you have a medium-sized business, a managed security provider will handle it for you. It can assist with:
- Setting up firewalls
- Antivirus protection
- Training employees
- Managing mobile devices
- Multi-factor authentication
- Handling backup and recovery
- Assessing network vulnerabilities
If security is a concern, but you don’t want to pay the costs of a managed security provider, you can hire a consulting firm to audit your system for weaknesses.
When hiring a cybersecurity service, be sure to do your research, find a company in your home nation that is well-known and has a good reputation. The cost will depend on the services you acquire, but you may find it cheaper than the salary of a full-time IT professional.
Additional Small Business Cybersecurity Tips
- Limit access to equipment: Especially any computers with sensitive information. Consider having a checkout and check-in process for equipment.
- Use permissions settings: Limit the access employees have to information or program software.
- Shut down computers every day: Have employees shut down or lock their computers before leaving for lunch or the day.
- Ask at-home employees to change their home Wi-Fi passwords: If employees are taking home work devices and logging on to their personal Wi-Fi, you’ll want it secure as well.
- Use unique usernames for each account: It may take extra work to come up with a unique username for each online account you have, but if one were ever to be breached, you wouldn’t want that same username for several accounts.
- Use 2-factor authorization when possible: This feature is when a second step is added to a login after entering the password—a text, phone call, or email—to confirm the user’s identity.
Glossary of Cybersecurity Terminology
- Adware: Unwanted advertising that shows up repeatedly on a screen—it is often difficult to remove.
- Botnet attack: Malicious software that enables a hacker to use your network without your knowledge, such as for sending spam.
- Breach: When a hacker successfully exploits a vulnerability in a computer or device and gains access to its files or network.
- Browser Hijacker: Malware that modifies a web browser’s settings without user permission. It can place unwanted advertising into the browser or replace homepages or search pages with the hijacker’s page.
- DDoS: Distributed Denial of Service Attack—flooding a website with malicious traffic or data to make it unusable.
- Firewall: Hardware or software that keeps unwanted programs from invading your computer or network.
- IP (internet protocol): An internet number unique to your location—like a home address, but for your computer.
- Keyloggers: Surveillance program to record keystrokes to discover passwords or sensitive information.
- Malware: Any software that intends to harm the software or user.
- Phishing: A technique to get sensitive information. Commonly an email impersonating someone and asking for financial information.
- Ransomware: These programs lock a victim out of their computer and usually come with a demand for money to release the computer.
- Spam: Another name for unwanted emails.
- Spyware: Software that lets a user steal sensitive information from a computer’s hard drive.
- Trojan Horse: A program that looks legitimate but can take over your computer to disrupt, steal, or damage your data or network.
- Viruses: A piece of code that can copy itself and corrupts a program, system, or data.
- VPN (virtual private network): A tool that masks your IP and encrypts your data, allowing you to stay anonymous on the internet.
- Worms: A program that spreads itself to other computers while doing damage to yours.
Bottom Line
Cybersecurity is easy to overlook—it typically isn’t a concern until something terrible happens to your business. The average cost to recover from a cyber-attack is $57,000. Especially now, small businesses can’t afford that. It’s worth investing in good antivirus, password manager, and VPN programs to secure your information and networks. Be sure to train your employees in the most common schemes and keep them update-to-date with current threats.